- Zero knowledge proof is technological advancement and introduces cryptographic protocols based on mathematical principles. .
- Zero-knowledge proofs (ZKPs) are cryptographic protocols that enable proving the validity of information without revealing sensitive data.
- Difference between two types of zk proofs: interactive and non-interactive zk proofs.
What is Zero Knowledge Proof?
“Zero-knowledge proofs (ZKPs) are cryptographic protocols that enable proving the validity of information without revealing sensitive data.”
This is the essence of Zero-Knowledge Proofs (ZKPs) – cryptographic methods that allow one party (the prover) to convince another party (the verifier) that a statement is true, without revealing any additional information beyond the truth of the statement itself.
Zooko, the co-founder of Zcash demonstrates Zk proof.
Zooko Wilcox used a simple analogy involving two hidden bits, challenging his partner to prove they were different without revealing their individual values. The process involved Zooko repeatedly swapping or not swapping the hidden bits behind his back, with the assistant correctly identifying the action each time.
He emphasized that after many repetitions, he became convinced the bits were indeed different, as a bluff (if the bits were identical) would eventually be exposed. Crucially, even after 100 trials, Zooko gained no information about the actual values of the bits (e.g., whether they were 0 and 1 or 1 and 0), only the single fact that they were different.
Basic Requirements Of Zk Proof Mechanism

A zk proof must fulfill two basic requirements: completeness and soundness. In Zk proof, completeness refers to the ability of the prover to demonstrate knowledge of the relevant information to a high degree of probable accuracy.
For the proof to be sound, the verifier must be able to reliably determine whether or not the prover is actually in possession of the information. Finally, in order to be truly zero-knowledge, the proof must achieve both completeness and soundness without the information in question ever being communicated between the prover and the verifier.
Brief History of Zero Knowledge Proof
The concept of a zero-knowledge proof was first described in a 1985 MIT paper, published by Shafi Goldwasser and Silvio Micali. They demonstrated that it was possible to prove some properties of a number without disclosing the number or any additional information about it. This paper also introduced the mathematically significant finding that interactions between a prover and a verifier could reduce the amount of information required to prove a given theorem.
A significant leap occurred with the publication of Bitansky et al by Nir Bitansky, Ran Canetti, Alessandro Chiesa, and Eran Tromer. This work was instrumental in advancing the field towards Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge (ZK-SNARKs).
In 2013, Pinocchio paved the way for Practical Verifiable Computation. Bryan Parno, Craig Gentry, Jon Howell, and Mariana Raykova, further solidified the practicality of ZK-SNARKs. Pinocchio was a built system for efficiently verifying general computations, offering a concrete implementation that demonstrated efficient verification and compact proof size (only 288 bytes, regardless of computation complexity).
It was one of the first systems to show that verification could be cheaper than native execution for some applications, and it introduced an end-to-end toolchain for compiling C programs into verifiable computations.
Groth16, published by Jens Groth, became one of the most widely adopted and highly optimized ZK-SNARK schemes. It significantly improved performance over previous designs like Pinocchio, particularly for arithmetic circuits. While it has greatly benefitted the development of zk proof it requires a trusted set up.
In 2015, Zcash was born and the application of zk proof technology widened.
A critical aspect of Zcash’s early implementation was the “trusted setup” or “Zcash Ceremony. The protocol embarked on building sophisticated cryptography. The introduction of Zcash introduced multi-party computation to generate secure public parameters, minimizing the risk of compromise.
The year 2017 saw the introduction of “Bulletproofs” [BBBWHM17] by Benedikt Bunz, Jonathan Bootle, Dan Boneh, Andrew Poelstra, Pieter Wuille, and Greg Maxwell. A key innovation of Bulletproofs is their ability to generate logarithmically sized proofs without the need for a trusted setup.
This transparency significantly reduces the trust assumptions required.
Bulletproofs are particularly efficient for range proofs, which verify that a secret number lies within a specified range without revealing the number itself, making them suitable for confidential transactions in cryptocurrencies like Monero.
Two Type of ZK Proofs
There are two distinct types of ZK proofs, namely interactive and non-interactive, each offering unique approaches to validating information securely without revealing sensitive details.
Interactive ZK Proofs
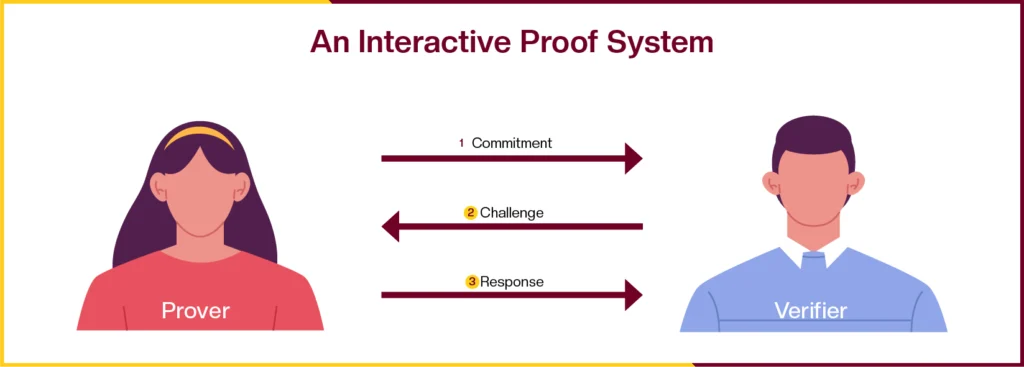
In this type the verifying party and the proving party engage in a back and forth communication to prove the validity of a statement. This type of zk proof is ideal for transactions or communication that are more complex and requires both the parties to be involved. This exchange may be repeated multiple times to increase the verifier’s confidence that the prover truly knows the secret.
The biggest advantage of using interactive zk proofs is that you do not need to invest in a trusted set up where each and every user on the network is governed by an administrator. This makes interactive zk-proof a better option for using it in scenarios where global compliance needs to be met.
Non-interactive ZK Proofs
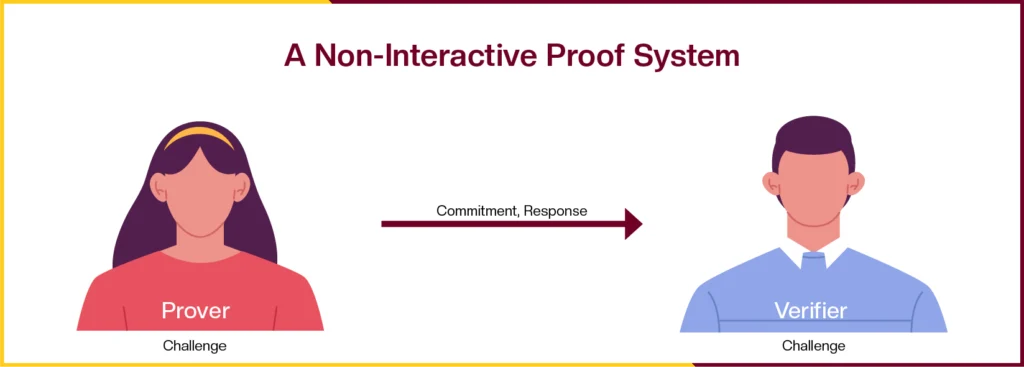
In non-interactive zk proofs the party that wants to get an input validated simply shares the input and if the input is correct the other party says it is accurate/ correct. As the term non- interactive suggests, this type of communication is limited and does not require back and forth communication between both the parties.
Non-interactive proofs eliminate the need for back-and-forth communication between the prover and verifier, offering a streamlined verification process. However, this “simplicity” pertains to the interaction model, not necessarily a reduction in computational complexity. Often, these proofs rely on a trusted setup phase or specific cryptographic assumptions to ensure their security and validity.
In essence, Non Interactive Zero Knowledge Proof (NIZKPs) are a fundamental building block for privacy-preserving and verifiable systems in an increasingly digital and decentralized world. They allow us to trust claims without having to blindly trust the source or reveal sensitive information.
Historically, many non-interactive ZKPs (specifically, certain ZK-SNARKs like Groth16) have relied on a “trusted setup.”
A trusted setup involves a one-time, multi-party computation to generate public parameters (known as a Common Reference String or CRS) that are crucial for the security of the proof system.
The “trusted” aspect refers to the critical assumption that during this setup, certain secret random values (“toxic waste”) were verifiably destroyed. If these secrets were retained by any participant, they could be used to forge invalid proofs, completely undermining the system’s integrity.
While complex multi-party ceremonies have aimed to mitigate this risk by distributing trust, the inherent requirement for some level of trust in this initial phase has remained a point of concern.
How Does Zk Proof Technology Work?
Zero-Knowledge Proofs (ZKPs) fundamentally rely on advanced cryptographic primitives to enable one party (the prover) to convince another (the verifier) of the truth of a statement without revealing any information beyond the validity of the statement itself.
Zk Proofs use polynomial commitments and elliptic curve cryptography. Lets understand this with an example. Imagine you have a complex mathematical problem, and you want to prove you know the solution without actually showing the steps or the answer.
In a ZKP system, the “problem” is transformed into a polynomial equation. The prover then constructs a polynomial commitment – a short, fixed-size representation of a polynomial that “commits” to its values without revealing the polynomial itself.
This commitment is analogous to sealing a folded piece of paper with the solution inside; you can’t see the solution, but you’re assured it’s there and hasn’t changed.
This is like embedding a solution that needs to be solved by the verifier. The missing areas in the equation is where the answer will go. If the person who wants to validate his or her input is indeed sharing the right data then he or she will be able to validate it.
The “zero-knowledge” aspect comes from the fact that the polynomial commitment and the verification process only reveal whether the committed polynomial satisfies the required properties, not the polynomial’s coefficients or the secret witness used to construct it.
This is akin to a magician proving a card is in a specific position in the deck without showing you the card itself or how they knew its position. The “proof” is a short cryptographic string that the verifier can check quickly, regardless of the complexity of the original statement.
Lets understand the technical aspect of the elliptical curve with an example.
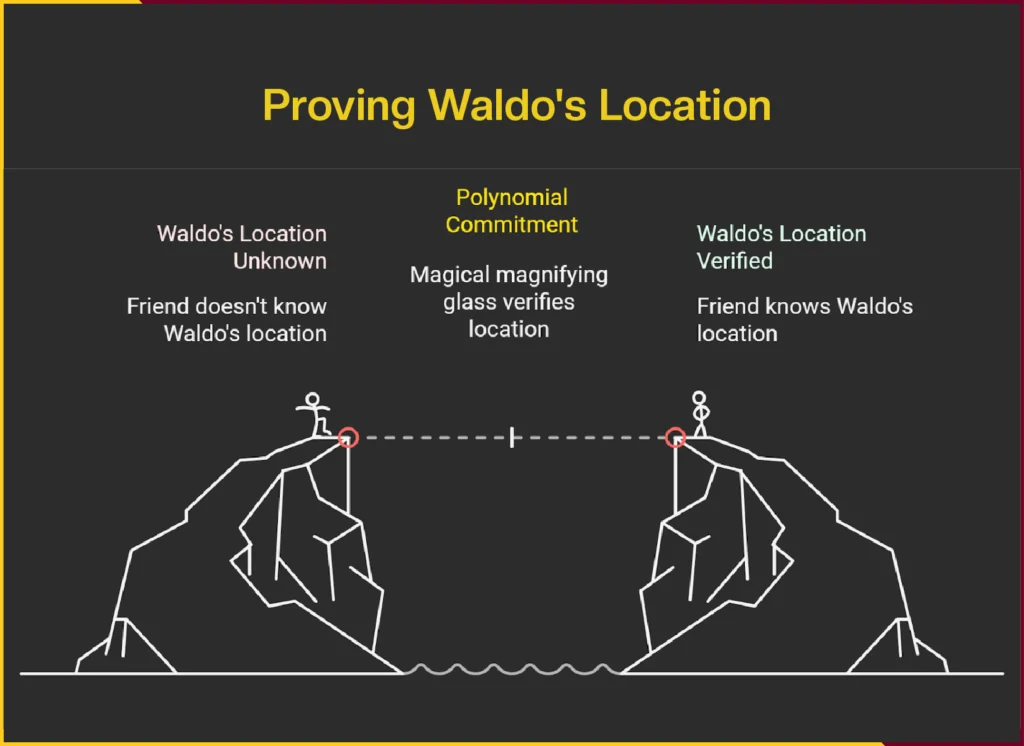
Imagine you have a giant “Where’s Waldo?” book. You’ve found Waldo on a specific page, but you want to prove to your friend that you’ve found him without actually showing them the book or pointing to Waldo.
Why? Maybe it’s a game, and you don’t want to spoil the fun for them to find him themselves, or perhaps the book contains sensitive information you don’t want to reveal.
So, finding Waldo becomes the problem statement here. Your knowledge of Waldo’s exact location on the page is the “solution” or “secret witness.”
So, how do you prove Waldo’s existence in the book? Using magic. Yes, it sounds out of the world, but it is true. Let’s understand this in detail.
Instead of showing the book, you have a special, opaque, magical magnifying glass. This isn’t just any magnifying glass; it’s designed so that when you place it over the page where you’ve found Waldo, it glows green if Waldo is indeed directly under it, and red if he’s not.
The key is that it only tells you “yes” or “no” – it doesn’t show you Waldo, the page, or any other part of the book. This magical magnifying glass is your polynomial commitment. It’s a compact, unrevealing representation of your knowledge.
Now, let the magic begin. In zk proof elliptical cryptography opens doors for data verification with limited knowledge sharing (to preserve confidentiality).
You let your friend hold the magnifying glass and place it over the exact spot where you claim Waldo is. If it glows green, your friend is convinced you know where Waldo is. They’ve verified your claim without ever seeing Waldo, the page, or the entire book. They’ve only confirmed the truth of your statement (“Waldo is at this spot”).
Applications & Use Cases For Zero Knowledge Proof
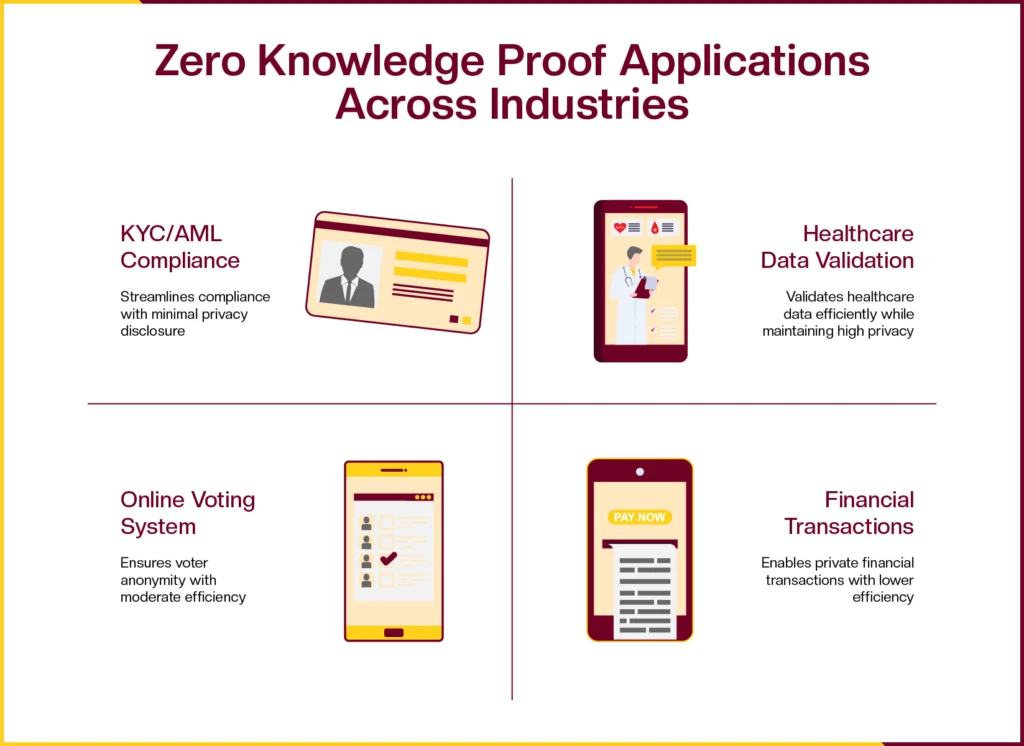
Compared to layer 1 blockchains, zero knowledge proof based protocols have a range of benefits that can be beneficial for industries like banking, identity management service providers, healthcare and supply chain management.
In this section, we will explore the various use cases for zero knowledge proof.
Financial Services
Confidentiality in transactions: In crypto, private transactions can be enabled. This function will allow you to hide certain details like sender, recipient, amount etc. This function will allow you to verify the transaction without having to disclose any confidential information. Examples: Zcash, ING Bank’s ZKRP for mortgage applications to prove income within a range without revealing the exact salary.
KYC & AML Verification
Streamlining compliance by allowing individuals to prove they meet KYC/AML requirements (e.g., “I am over 18,” “I am a resident of X country”) without disclosing their full identity documents or sensitive personal data to every service provider.
Identity Management & Authentication
One of the most important applications of zk proof is using it in identifying management systems that allow for seamless and private verification processes. This application makes the whole process of verifying identity secure as users do not have to share all details pertaining to their existence. Simply proving that their identity is valid is enough to pass through the identification system.
Healthcare & Supply Chain Management System
Zk proof allows healthcare providers to validate patient records, insurance eligibility, or medical certifications without exposing sensitive patient information. Furthermore, zk proof also allows researchers to verify aggregated data or specific attributes within datasets without compromising individual patient privacy.
In the supply chain, zk proof can be used for a range of use cases. Supply chain management helps in identifying the origin, journey, and authenticity of products without revealing proprietary trade secrets or sensitive supplier details. This can combat counterfeiting and ensure ethical sourcing.
In addition, zk proofs can also help in proving adherence to regulations, quality standards, or sustainability practices throughout the supply chain without exposing confidential business information.
Online Voting System
Voting management systems automated with zk proof can enable voter anonymity as it allows voters to cast their ballots and have them verified as legitimate without revealing their identity or vote, ensuring both privacy and election integrity. It enables public verification of election results without compromising individual voter privacy.
Protocols Using Zero Knowledge Proof
Some of the most popular platforms that use zk proof technology are for example Loopring, Immutable X and Starknet and ZkSync.
Loopring
Loopring is a decentralized exchange (DEX) protocol that utilizes zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge) to enable high-throughput, low-cost trading. It processes order book management and transaction execution off-chain, ensuring security through on-chain verification of ZKPs.
Immutable X
It is a layer 2 scaling solution specifically designed for NFTs and blockchain gaming. By employing ZKPs, Immutable X offers instant, gas-free NFT minting and trading, addressing the scalability and cost issues previously hindering the widespread adoption of NFTs on Ethereum.
Starknet
Starknet is a decentralized validity rollup (zk-rollup) that uses zk-STARKs (Zero-Knowledge Scalable Transparent Arguments of Knowledge) to achieve massive scalability for any dApp. It is important to note that this infrastructure does not need a trusted set up to function. Starknet executes transactions in bulk and uses STARK proofs to allow the Layer 1 (Ethereum) to verify these transactions with minimal computational effort, emphasizing accuracy and efficiency.
Risks & Challenges in Zero Knowledge Proof
Following are some of the major challenges prevalent in implementing zk proof technology in day to day life.
Generating ZKPs, especially for complex statements or large datasets, can be computationally very intensive for the prover. This requires significant processing power and time. While verification is generally fast, the proof generation process can be a bottleneck.
Submitting ZKPs to a blockchain incurs gas fees, though ZK-Rollups significantly amortize these costs across many transactions, making the per-transaction cost much lower than direct mainnet transactions.
The ZKP field is rapidly evolving, leading to a proliferation of different protocols, implementations, and cryptographic assumptions. There’s a lack of universal standards for how ZKPs should be constructed, integrated, and made compatible across various platforms.
The privacy-enhancing nature of ZKPs, while beneficial for users, can raise concerns for regulators regarding anti-money laundering (AML), know-your-customer (KYC), and counter-financing of terrorism (CFT) compliance.
The ability to conduct transactions or prove attributes without revealing underlying data can be perceived as enabling illicit activities.
Wrapping Up
Zero Knowledge Proofs are a super useful and advanced piece of technology used in businesses and organizations for a different array of purposes. Multi party computation can be done in auditing firms by simply setting up a trusted network and updating the blockchain with audits and its related information without having to deal with a third party software.
In contrast to this, zk proofs can also be used in cases where users need to interact with each other in order to validate a transaction. Zk proof tech can be used in CBDCs, speculative crypto investing and identity management systems spanning across the globe. Zk proofs take decentralized blockchain application systems a notch higher.







